
Better security needed for online industrial machinery
Increasingly, industrial machinery is connected with the online world. Sensors in and near machines generate and transmit data to a back office, often in the cloud. Machines receive operational instructions and software updates remotely. The fear of falling behind competitors has resulted in a race to develop new online functionalities. But there is a downside to this trend. Online connections increase vulnerability to attacks. The consequences can be catastrophic: a successful attack can paralyze a company for weeks and cause millions of damage.
Risk of cyber-attacks
Industrial cybercrime is a serious business. Incidents often go unreported, but unfortunately some attacks are extremely successful. And it can affect anyone. One big international shipping company can testify to that. One day a malicious worm virus (in the guise of ransomware) spread across this shipping giant’s head office in a matter of minutes and switched off every computer. The company’s IT department ultimately needed ten days to restart all of them, and business was effectively on hold throughout that period. Only the most important shipments could be carried out with great difficulty. The total damage ran into the hundreds of millions of dollars, and there were other victims too. Dozens of companies were infected with the extremely advanced virus, and the American government estimates that the total damage worldwide amounted to ten billion dollars.
Who are behind it?
Cybercrime pays, that much is clear. Attackers are no longer the stereotypical idealistic hackers in their attic bedrooms. They have clear goals and are after money, for instance through selling stolen data. In addition, action groups are at work that use high-tech means to disrupt production or even to sabotage production sites to put pressure on large companies and influence them.
Probably the most dangerous actors in the field are so-called ‘state actors’. These organizations rely on the support of (foreign) governments and therefore have almost unlimited resources that allow them to launch very advanced attacks. Their underlying motives are sometimes economic, but also include espionage or sabotage, for instance of companies that manufacture high-grade electronics or military material.
Tip of the iceberg
A question we often get when we talk about cybercrime is: “Is the threat really that big?” An understandable question, because successful cyber-attacks are rarely publicized. One of the reasons for this is that companies who are affected try to minimize reputational damage through negative publicity. But the most important reason is much more troubling: in many businesses, monitoring and security are so defective that attacks are not even detected! Media reports of cyber-attacks are only the tip of the iceberg.
Online brings advantages – and risks
Over the last few years, the number of online applications has increased exponentially, also for industrial machinery. There are a lot of advantages to this and in fact it is an indispensable step toward Industry 4.0 or Smart Industry. Remote operation makes it possible to control devices from a single central control center. Log files and data derived from machines can be sent to the user’s or supplier’s back office, where they can be used for monitoring and optimization. Support and maintenance of machines is also increasingly done remotely: maintenance and upgrades of built-in software are often carried out through online connections.
Vulnerability to attacks is directly proportional to increased connectivity. In the general excitement about the opportunities, these risks are often overlooked. To give one example: if measuring systems are installed on a piece of equipment that can be read out remotely, who has access to this data? What are the consequences if the data were to fall into the wrong hands?
Another risk, especially for manufacturers of machinery, lies in the operating software of machinery – the Intellectual Property or IP. How well is the software protected against copying or tampering? And is this protection adequate if the device in question is going to be used on the other side of the world, out of the manufacturer’s sight? The last thing any manufacturer wants is for his machinery and operating software to be cloned by some foreign pirate.
In our experience, the situation is almost always more complex than the client initially thinks. The figure below shows how online components in a fictitious industrial environment are linked to each other. Each point where outside access is possible forms a potential security risk.
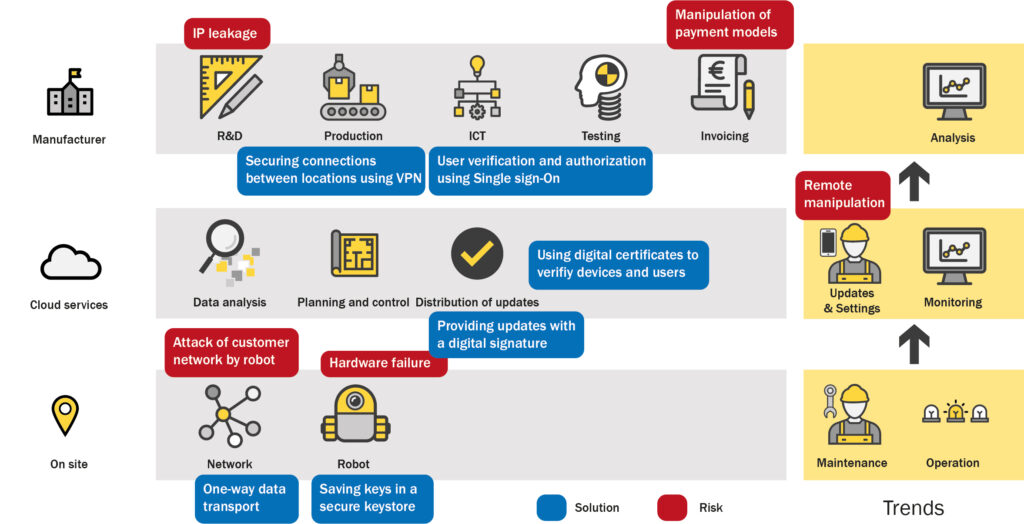
A structured approach is effective
It is possible to mitigate the security risks of online devices. The crucial point is to choose a structured, step-by-step approach. This requires a thorough inventory of all vulnerabilities. What online functionalities are already there or will be developed, and what security risks does this entail? Are there mutual connections and dependencies between machines, applications, and storage systems that are not immediately visible? To what extent must external parties be given access? How is this access monitored? A good security solution will take all of these aspects (and others) into account.
Once all risks have been mapped and prioritized, it is possible to take effective measures. There are usually several security options. For instance you could work with a VPN (Virtual Private Network) for secure connections, or install two-factor authentication for the system’s users. Verification of users and devices can be done through certificates and a so-called Public Key Infrastructure. It would take us too far afield here to describe all possible risks and the corresponding measures. An expert partner like Technolution can advise for your specific case.
